Introduction
The RE&CT framework is an open-source project that accumulates, describes, and categorizes actionable Incident Response techniques. Who will need this? SOC (Security Operations Center) Analysts, security professionals and other people responsible for responding to cyber incidents. In a nutshell, the project helps companies understand and list what actions are available for them to prepare and respond to a cyber incident.
PICERL
RE&CT is based on the PICERL a six-step framework:
All 6 stages of IR (Incident Response) will be summarized in the next paragraphs while adding some examples with RE&CT IR techniques. The following article developed by Tanium describes PICERL framework. https://www.tanium.com/blog/are-you-prepared-for-a-security-incident-here-are-six-steps-to-help-you-be-ready/. The RE&CT framework completes the PICERL framework by adding response actions to each of these stages. This will help you get your actual coverage and document how to proceed on each stage of incident response and ensure an identical operating mode throughout the organization, as well as a consistent result for a given operation. An MSSP may need to describe the response actions for each of their customers, because they may have different solutions implemented, different tools, and different permission access to their network resulting in a different workflow of the security analysts.
1 Preparation
The first stage of the RE&CT framework lists the actions required before getting involved in an incident response. This stage of RE&CT contains 103 response actions.
For example, you can find response actions such as “Develop a communication map” or “Access VPN logs”.
2 Identification
Understand when it started, what was the entry point? What is the scope? Each of these questions must be responded to by the response actions in this stage. This stage of RE&CT Contains 63 response actions.
For example, you can find the response actions “List host vulnerabilities”, “list files downloaded” or “Analyze PDF file”.
3 Containment
Prevent unwanted behaviors from spreading. This stage of RE&CT Contains 26 response actions.
As examples of response actions, we find: “Quarantine file by hash” or “lock user account”.
4 Eradication
Remove the malicious instances. This stage of RE&CT Contains 8 response actions.
Here are some examples of response actions “Revoke authentication credentials” or “Delete email message”.
5 Recovery
Recover from the incident and return all the assets back to normal operation. This stage of RE&CT Contains 14 response actions.
Here are some examples of response actions “Restore quarantined file” or “Restore data from backup”.
6 Lesson Learn
Opportunity to review and document what you learned about the breach. This stage of RE&CT contains 2 response actions “Develop Incident report” or “Conduct lessons learned exercise”.
RE&CT Navigator
All the response actions are accessible through an interactive navigator https://atc-project.github.io/react-navigator/. You can use it to visualize your coverage and understand the gap in your process of incident response by example selecting green for the response actions available and red for response actions unavailable.
Playbooks
You can aggregate and organize these response actions for specific incident response cases and create what we call playbooks. A Playbook is a list of tasks that must be executed to respond to a specific threat. Here is an example of a phishing email with a non-exhaustive list to just emphasize the use case of a playbook.
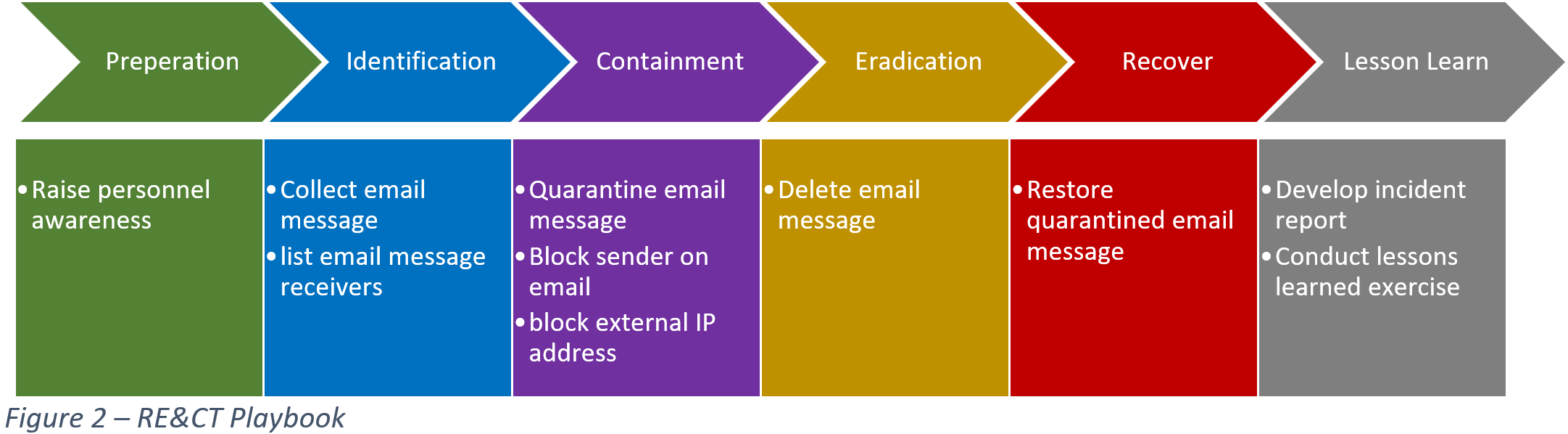
The playbook created with the PICERL framework will cover each stage of the incident response with a list of different available actions.
Limitation of RE&CT framework
RE&CT framework is a project still ongoing and for now, there is a lack of playbooks, only one playbook for phishing email attacks is suggested. Some response actions look redundant, and in some specific cases, response actions are not mentioned and should be added.
Conclusion
The RE&CT framework could be helpful to understand and visualize the network coverage. Unfortunately, minor flaws could be fixed like redundancy in some Incident Response actions as well as the lack of specific use case that are not mentioned.
However, this project is worth spending time and effort since it is entirely cost-free which makes it a valuable resource despite these minor flaws. Filling out all the response cases and understanding your coverage will be fairly quick.
For more details, check out the official git project https://github.com/atc-project/atc-react.